Date: July 27, 2021
Category: News
Autor: Ewelina Kaatz-Drzeżdżon and Paula Saameño Pérez
Governmental users from EU Members States, as well as EU agencies and institutions will gain access to secure and cost-effective communications capabilities under the European Union Governmental Satellite Communications (GOVSATCOM) initiative in the near future. Access to guaranteed and secure SatCom services can be vital in case of any interruption of terrestrial network services (e.g., in disaster areas), unavailability of other communication links (e.g., in maritime areas or in the Arctic region), for humanitarian missions in hostile territories or for the operation of critical infrastructures. Accordingly, security-related considerations play a central role in the design of the GOVSATCOM system and services for prospective users operating in critical scenarios. A user consultation process, which has been carried out within the ENTRUSTED project, is expected to play an instrumental role in capturing user expectations regarding core features and aspects of GOVSATCOM.
Satellites, ground stations and other space assets become more vulnerable to cyber attacks with increasing reliance on the Internet and other cyber networks [1]. Therefore, cyber security and information protection represent the backbone of any secure SatCom system. Cyber security allows to preserve the availability and integrity of infrastructure and networks, while information protection ensures the confidentiality of exchanged information [2]. Developing a secure space-based connectivity system is a complex challenge that requires a multifaceted approach. Cyber resilience is a new buzzword in the field of secure SatCom. It determines the ability of the system to adapt to changing conditions, as well as to prepare for, respond to and recover from any disruption caused by cyber attacks [3]. Indeed, the European GOVSATCOM system will have to meet multiple and advanced security requirements to guarantee the protection of information and the continuity of service.
Common SatCom threats
SatCom networks and systems (i.e., space, ground and user segments) are prone to various attacks which may result in the disruption of services, malicious control over services, data alteration or information leakage. SatCom networks can be degraded by the introduction of noise or interference, both intentional or unintentional. Threats to SatCom systems and transmitted data take many forms, including malware which infects a system or a sophisticated cyber attack on critical components [4]. Malware can destroy the system, saturate the network or reroute the communications. Unauthorised access may cause the disclosure of sensitive information, signal being broadcasted to unwanted users, reception or transmission of modified information, or even the loss of communication [5]. Data communications can be disrupted through jamming, eavesdropping, hijacking or spoofing [6]. Even some instituted security measures can be subject to a malicious cyber activity. This can be exemplified by hacking, damaging or interfering with encryption and authentication protocols.
GOVSATCOM demands an effective protection of SatCom networks and systems, security of transmitted data and information, and resilience to system failure or cyber attacks. End-to-end secure solutions are essential to ensure that the required security levels are met, in line with actual requirements defined by users.
Identifying security-related needs of GOVSATCOM users
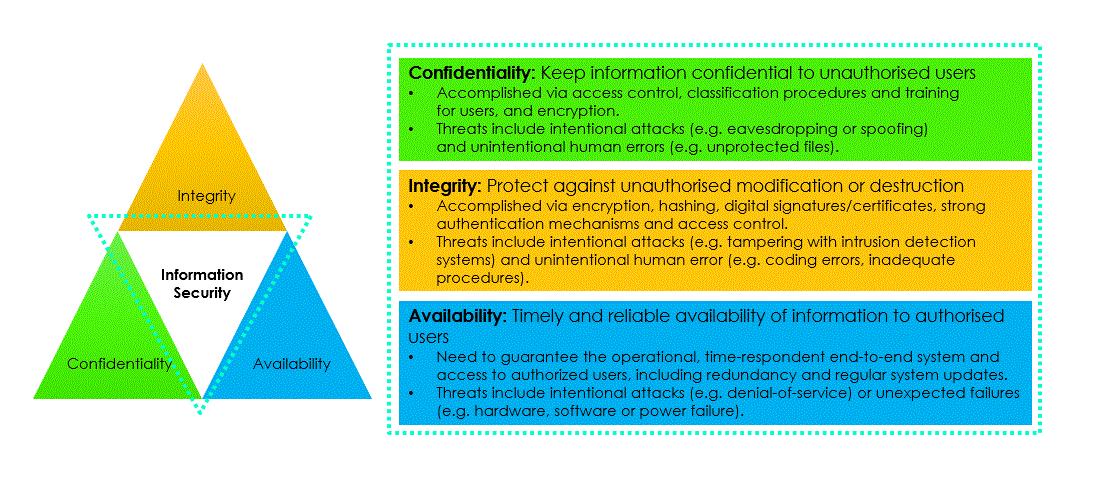
A survey study conducted among prospective GOVSATCOM users between April and July 2021 represents a pivotal part of the user consultation process within the ENTRUSTED project. Members of the ENTRUSTED Consortium and external collaborators carried out the survey [7] among governmental and institutional users, who were requested to specify their needs and expectations regarding the anticipated GOVSATCOM capacities, services and their attributes. An essential part of the survey study focused on security-related issues. Security was addressed in relation to information protection, including the protection of data (either in transit, or stored), and the access to SatCom services and infrastructure, covering space, ground and user segments. The choice of reviewed security aspects was informed by the CIA triad – Confidentiality, Integrity and Availability – which is an information security model commonly applied in the development of IT security policies [8]. These were complemented with non-repudiation (i.e., the inability to deny any event or action) and authenticity (i.e., a guarantee that information is genuine and from bona fide sources) [9] – both closely related to integrity.
Confidentiality is ensured when data is protected from unauthorised access using, for instance, file encryption and access levels. Protecting data from any unauthorised modification is necessary to preserve their integrity. Hence, integrity is about safeguarding the accuracy and completeness of transmitted information. While availability means that data should be accessible to authorised users as and when required. A general overview of the CIA triad is presented in Figure 1.
Figure 1: The CIA triad
Initial survey questions were intended to provide insights into the overall security needs of prospective GOVSATCOM users. Respondents were asked about the relevance and importance of various security considerations for their foreseen usage of secure SatCom services. Information obtained from the survey will be subject to an initial analysis and prioritisation of high-level security needs.
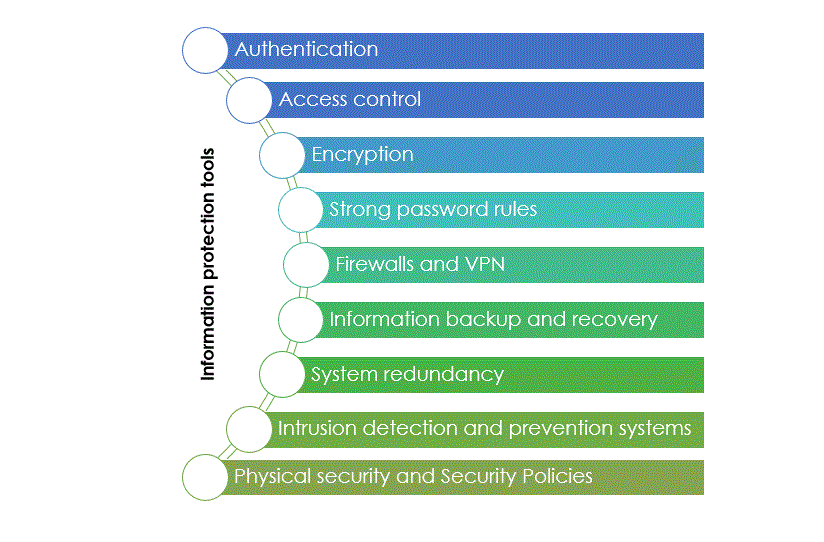
Subsequent survey questions allowed for the indication and prioritisation of required information protection means, including solutions necessary to guarantee the access to SatCom services in a secure manner. Such solutions may comprise authentication and access control methods, encryption tools with different levels of security, strong password rules, regular backups of information and redundancy in systems, software protection via firewalls or the implementation of Virtual Private Networks (VPN), physical security solutions, or security policies and procedures at the EU and organisation levels (e.g., regarding the EUCI). The most common information protection means implemented in communications and information systems are listed in Figure 2.
Figure 2: Information protection tools used in communications and information systems
The survey study also analysed security needs in specific use cases declared by respondents. Survey participants were presented with a list of considerations comprising: resilience (i.e., a system’s ability to regain its status after any interference or interruption), robustness to interference (i.e., the elimination of unwanted signals), anti-jamming (i.e., prevention against signal disruption), cyber resilience and the protection of information on the level of users’ information systems, data encryption, controlled access to services, infrastructures and control centres, non-dependence on third parties, authenticity, and non-repudiation. If any outlined use case was associated with some safety-related applications (e.g., EGNOS (ARAIM), ATM (SESAR)), there was a possibility to specify additional security aspects. Respondents were also queried about the EUCI level of information exchanged during operations conducted in the respective use case.
Security-related aspects were also examined in the context of their impact on business or operations, in terms of the criticality of any service degradation or interruption for each declared use case. Respondents could indicate a relevant level of criticality for the following aspects: confidentiality, integrity, availability, and resilience to jamming or spoofing. Feedback obtained from prospective users is key for the identification of potential requirements that will have to be considered in specific GOVSATCOM services.
The ENTRUSTED survey study provided a unique opportunity for governmental and institutional users, both inexperienced and experienced in accessing secure SatCom services, to share their expectations regarding future GOVSATCOM services and key features. Most importantly, the survey allowed users to indicate their minimum acceptable security levels for accessing secure SatCom services in general, in specific use cases or applications, in a short-term perspective and after 2027. Information from the survey will allow to implement adequate security-related solutions following a stepped approach [10] in the design and development of GOVSATCOM.
User requirements for a GOVSATCOM service portfolio
The ENTRUSTED Consortium and external collaborators collected survey responses until the end of June 2021. Received answers are being currently aggregated and analysed. Survey results will be presented in the form of a consolidated set of user requirements concerning the provision and access to GOVSATCOM services. These requirements will represent the user perspective and indicate market conditions that drive them.
Understanding user requirements is indispensable for the development of a user-oriented GOVSATCOM service portfolio. Requirements derived from the ENTRUSTED survey will be submitted to the European Commission as the User Requirements Document (deliverable D2.3) in the beginning of 2022. This document will include sensitive information and its dissemination will be restricted in line with the recommendations by the European Commission.
References
[1] Housen-Couriel, D. (2016) Cybersecurity threats to satellite communications: Towards a typology of state actor responses, Acta Astronautica, Vol. 128, pp. 409-415, https://www.sciencedirect.com/science/article/abs/pii/S0094576516301552
[2] European Commission (2016) Operational Guidance for the EU’s international cooperation on cyber capacity building, Publications Office of the European Union, Luxembourg, https://www.iss.europa.eu/sites/default/files/EUISSFiles/Operational%20Guidance.pdf
[3] IT Governance, Cyber Resilience, https://www.itgovernance.co.uk/cyber-resilience
[4] iDirect Government (2020), Cybersecurity in SATCOM – Taking a Defense in Depth Approach, White paper, Version 1, http://www.idirectgov.com/
[5] European Commission (2016) Satellite Communication to support EU Security Policies and Infrastructures. Final report, Ref. Ares(2016)1563278 - 01/04/2016, Directorate-General for Internal Market, Industry, Entrepreneurship and SMEs, Brussels.
[6] Manulis, M., Bridges, C. P., Harrison, R., Sekar, V., and Davis, A. (2021) Cyber security in New Space. Analysis of threats, key enabling technologies and challenges, International Journal of Information Security, Vol. 20, pp. 287–311 https://link.springer.com/article/10.1007/s10207-020-00503-w
[7] ENTRUSTED Consortium (2021) In the quest of user-centric GOVSATCOM, https://entrusted.eu/news-events/news/space-programme-2021-2027-gives-new-prospects-3
[8] DNV (nd) The three-pillar approach to cyber security: Data and information protection, https://www.dnv.com/article/the-three-pillar-approach-to-cyber-security-data-and-information-protection-165683
[9] Council decision 2013/488/EU on the security rules for protecting EU classified information (2013), Official Journal of the European Union, L 274/1, EUR-Lex - 32013D0488 – EN, https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A32013D0488
[10] Regulation (EU) 2021/696 of the European Parliament and of the Council establishing the Union Space Programme and the European Union Agency for the Space Programme and repealing Regulations (EU) No 912/2010, (EU) No 1285/2013 and (EU) No 377/2014 and Decision No 541/2014/EU (2021), Official Journal of the European Union, L 170/69, https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=CELEX:32021R0696&from=EN
